DrayTek Vigor 2860 to 3900 IPSec VPN
This example is useful when connecting a VDSL/FTTC satellite office (with a Vigor 2862/2860) to a Dedicated Ethernet Fibre (Vigor 2960/3900) Hub Office with a secure IPSec VPN. Both offices have a static IP in this example and are available for us to configure at the same time...
Firstly we shall configure the hub Vigor 3900 router at the hub office endpoint for the satellite office to connect to.
Firstly login as normal to see the home screen:
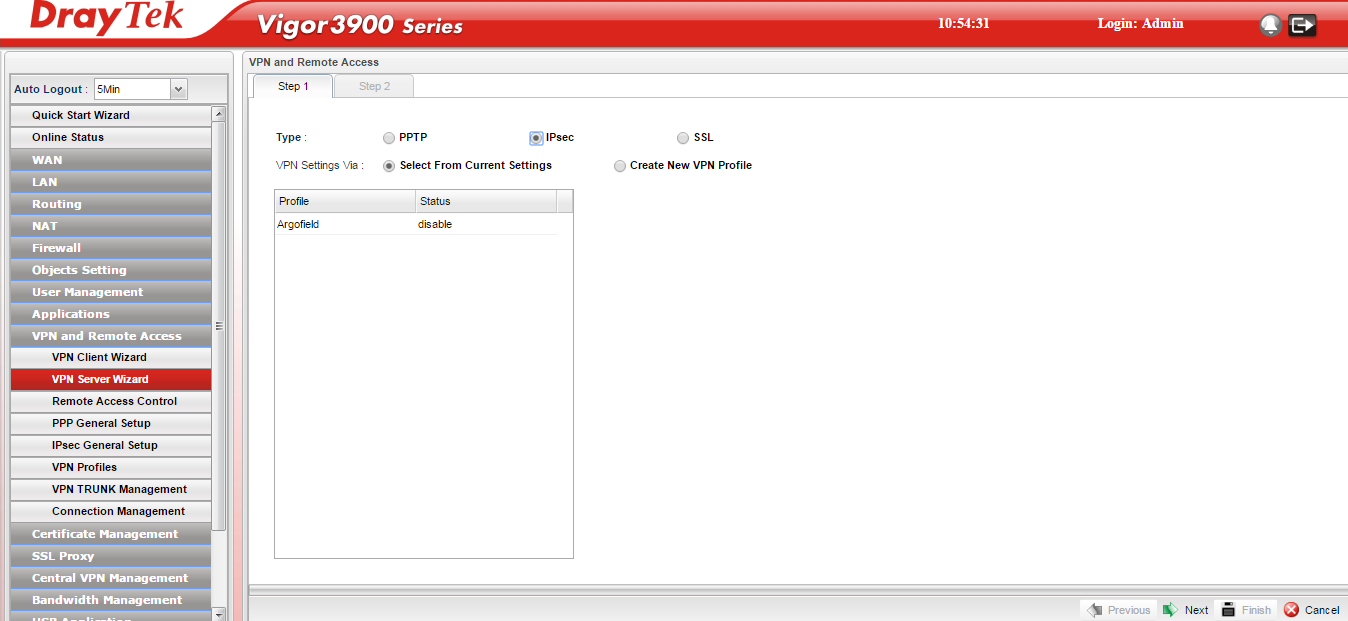
Now go to VPN and Remote Access and choose VPN Server Wizard and select IPSec as your VPN type:
Click to select creating a new VPN profile, choose a name - I have called this one HubOffice - and click next:
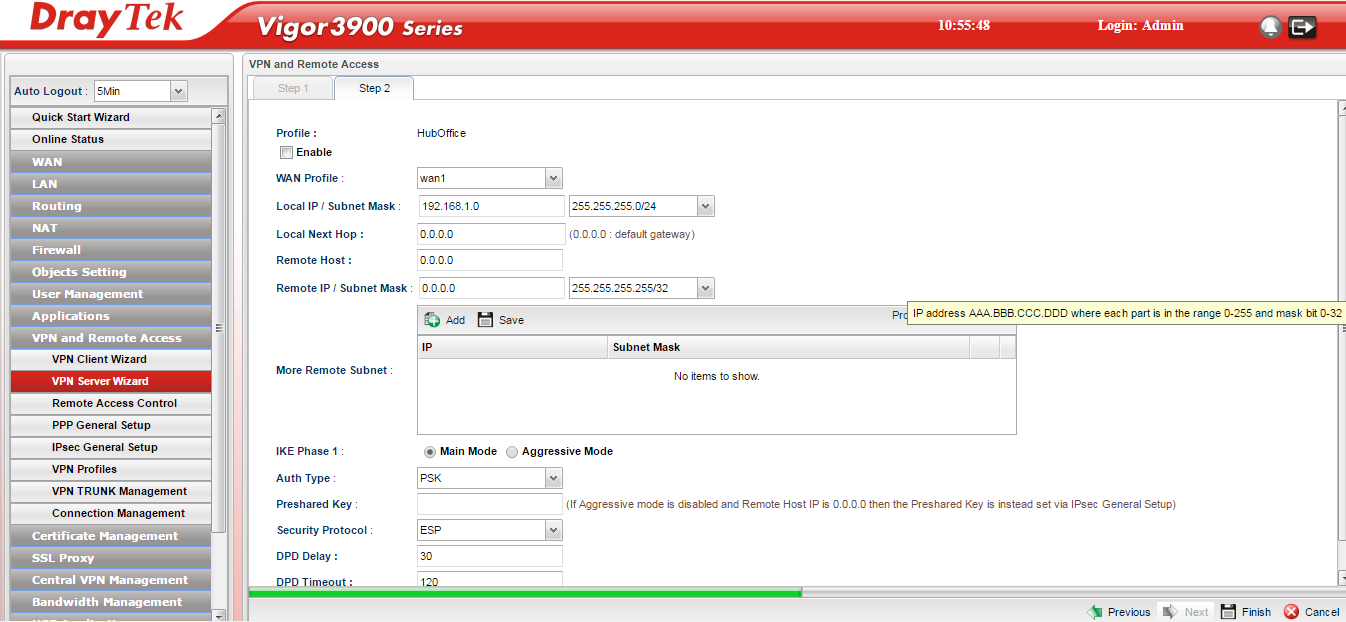
Now we are going to enter the VPN specific information to allow our satellite office to connect:
- Tick the Enable box to enable the VPN
- Choose the WAN port you are using for the internet connection that will carry the VPN and for which we will be using the external IP address of
- Enter the local subnet - this is not provided automatically so enter your local subnet that the satellite office is being provided access to - this may well be the subnet you are using
- Leave the next hop as 0.0.0.0
- The remote host is the external WAN IP of the satellite office Vigor 2860
- The remote host IP/subnet mask is the internal LAN subnet of the Vigor 2860 LAN
- If there are any other subnets hung of the back of the Satellite office - if it is a hub in itself - then you can add the extra subnets here but this can often be a hinderence in getting the VPN to come up so we shall leave it blank for now.
- Auth type is PSK for passphrase/shared secret that we will enter momentarily
- Pre-shared key - enter a long string that you have made a note of, as it is to be entered in the 2860 router later
- Security protocol - leave at ESP
- We are leaving the DPD delay and timeout boxes as default
Click finish to complete the setup...
You will be asked if you wish to proceed to the VPN status page and that is what we shall do:
Now we shall proceed to configure the 2860 which has a similar interface:
We won't use the VPN Client Wizard so that you can see all of the steps, we will configure the VP manually, click VPN and Remote Access > LAN to LAN:
then select a number corresponding to the profile you wish to configure:
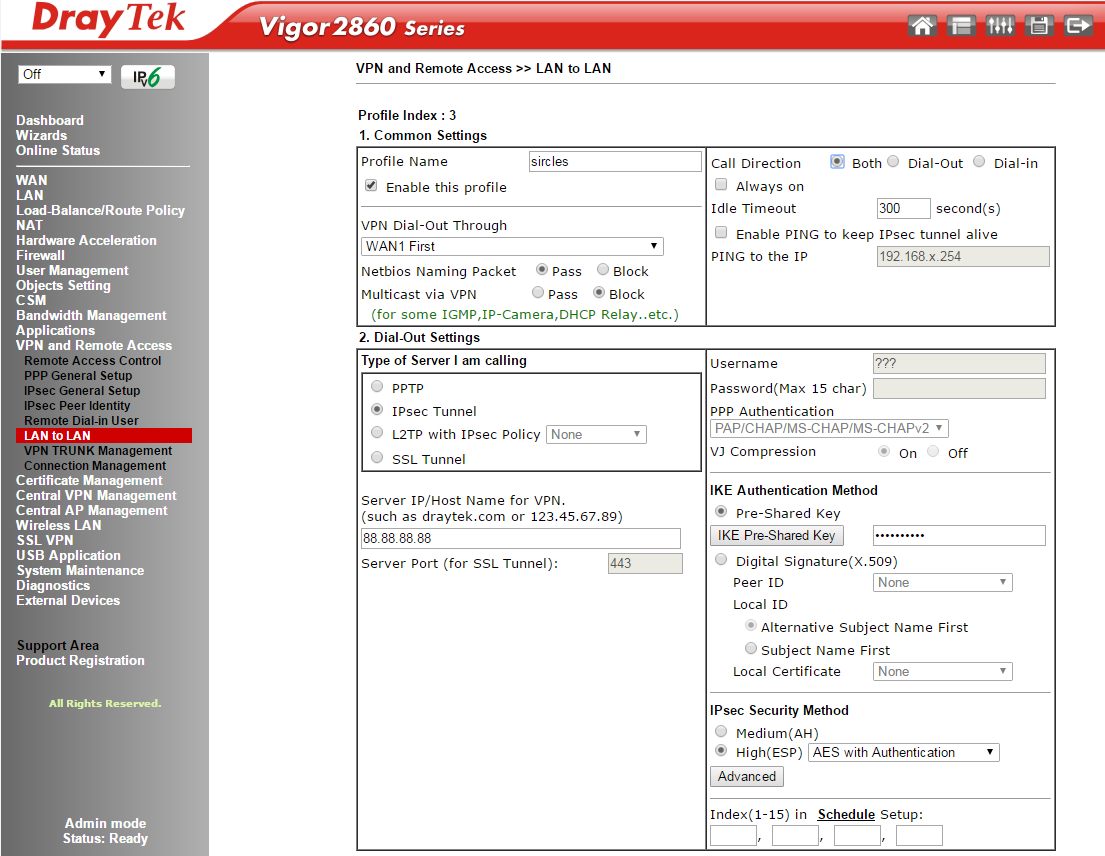
- First tick the Enable box to enable the profile
- Give the profile a name
- Choose the WAN1 interface for the VDSL interface if that is what you are using for the VPN external WAN IP address
- Click the pass NetBIOS box to allow ICMP traffic between the offices
- Leave Multicast blocked
- To the right of that leave the call direction as Both
- Below to the left select IPSec as the VPN type
- Below that, enter the IP address or A record host name of the hub office Vigor 3900 WAN
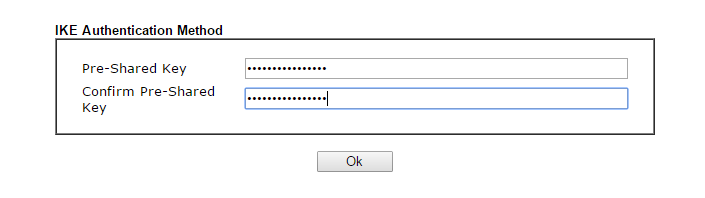
- To the right, click on the IKE Pre-Shared Key button and enter the key as you entered it into the DrayTek Vigor 3900:
- Now below that enter the IPsec method as High(ESP) AES with Authentication, then click the advanced button
- Click the option to enable PFS - perfect forward secrecy
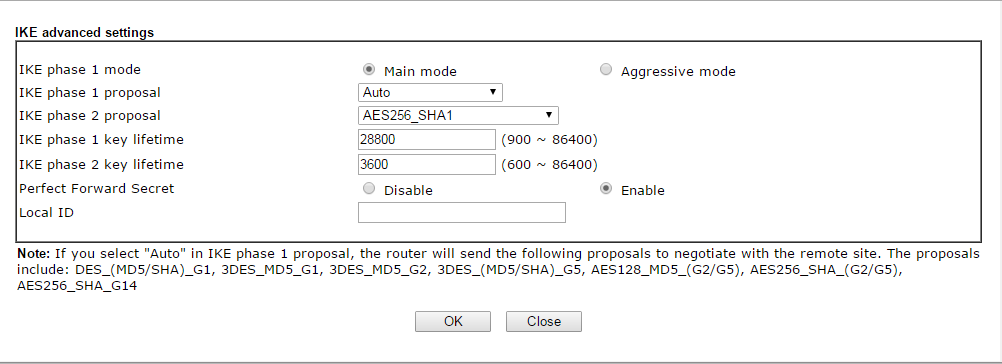
- Leave the other timeouts as they are and click OK
- Tick the box Specify Remote VPN Gateway and enter the 3900 WAN IP address
- Leave the GRE settings as blank and proceed to the bottom section 5.
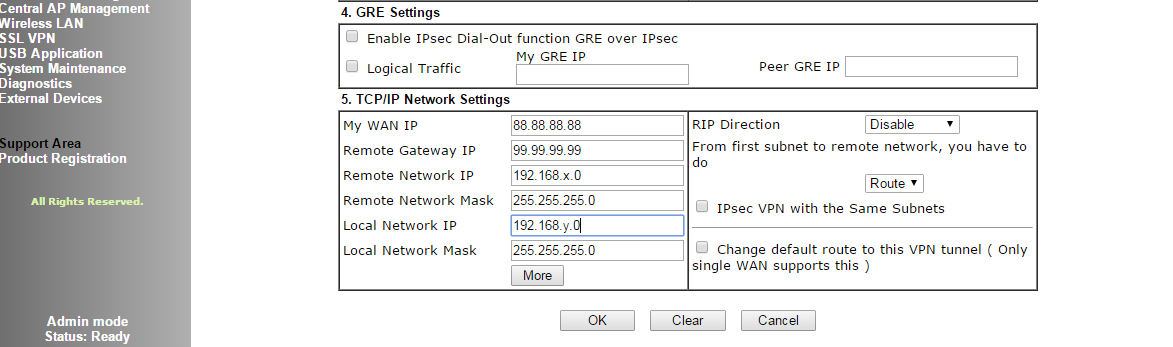
- Enter the 2860 WAN IP in the first box
- Enter the 3900 WAN IP in the second box
- Enter the 3900 LAN IP network address in the third box
- Enter the 3900 LAN subnet in the fourth box
- Enter the 2860 LAN network address in the fifth box
- Enter the 2860 LAN subnet in the final box
- Leave the RIP settings as they are.
Now you should be able to go to the connection status on either router and see that the connection is live and be able to ping the other office from each respectively...
Other VPN configuration pages: Sonicwall VPN to Draytek Vigor Cisco RVS4000 Draytek Vigor IPSec VPN