Securing Office 365
Office 365 is an open target.
It has many security flaws compared to Exchange, most significantly, that as soon as they see your email address (which may even be on a website) they most likely know your username.
They also know which IPs and domains to sniff by watching the content providers, and also know exactly how to access the system as soon as they have acquired credentials.
Office 365 also supports services like POP and IMAP so they can fire emails just from SMTP.
This is all pretty concerning if you have come from a world of IPv6 Exchange servers hidden behind Mimecast and their buddies.
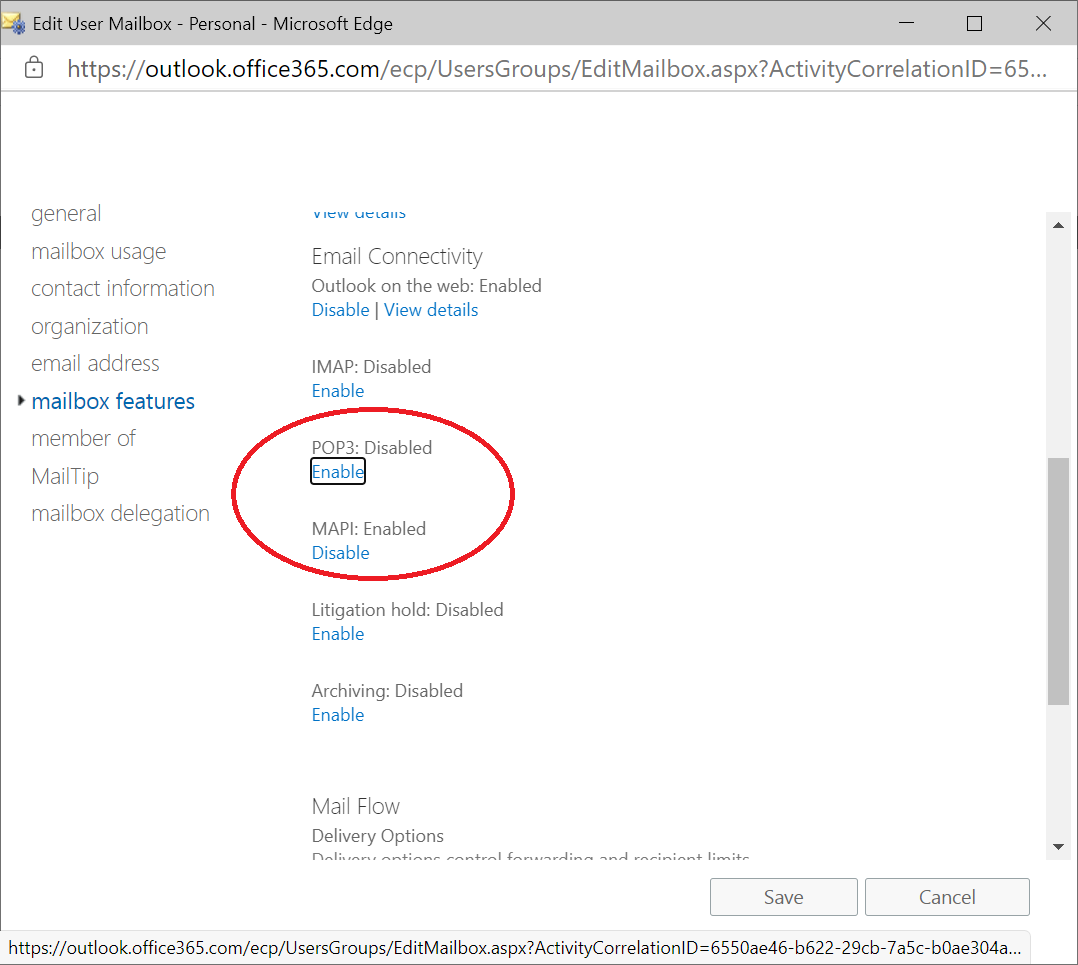
So let's start with a few basics, is anyone using POP or IMAP? If they are then why bother with Office 365? The Exchange collaboration tools make Outlook a must. Let's disable POP and IMAP..
Go to the Exchange Admin page into mailboxes, once there double click a recipient, then go to the Mailbox Features section and click the items to be disabled:
https://admin.microsoft.com/Adminportal/Home?source=applauncher#/featureexplorer/security/SecurityDefaults
Now the next action is to add the Microsoft 2FA which still supports an SMS-based texting system that asks you to provide a code that is texted to your mobile phone at login. Having tested this we can confirm that although the text message system is fine, it is probably best to use the authenticator app that is available.
Here we are setting up the phone number for an account:

You are then given a password for applications that do not support the 2FA set-up, android mail for example.
