Windows Active Directory, DNS & DHCP with VPNs
When a VPN is set-up it is simply a connection between LAN subnets that allows certain traffic to be passed between them. If you are using a Windows Server Active Directory network then you need to make sure that you are adjusting your settings to maintain normal traffic and avoid any catastrophes like loopback etc.
Even some of the most down-to-Earth routers can trip you up with DNS and AD when it comes to VPN. DrayTek routers can connect two subnets with the same LAN Subnet but if the Windows servers start inter-communicating it can cause all sorts of issues at Layer-2 and 3. I would always recommend changing one subnet (or even both if they are x.x.1.x or x.x.0.x) rather than using route NATing between subnets.
Before you connect a VPN you should be treating the planning exactly as if you were running a cable between the two sites you plan to connect. Although a VPN arrives via a WAN connection, it is not necessarily subject to the same rules as the internet in the case of DrayTek routers unless you specifically tell the firewall to block certain services. If you are using a highly configurable router such as a Cisco or Juniper then you can configure all sorts of setting on the firewall specifically for that subnet, but if you are using a simpler router such as a home WiFi router or similar, then you will find that a VPN connection forwards most of the traffic between sites including all types of ICMP & NetBIOS. As a result you must be sure that nothing is allowed to connect to the other LAN that you would not wish to be connected to the existing LAN.
Active Directory is heavily dependent on DNS to locate the resources it requires in order to function and so, regardless of what is behind each VPN endpoint, DNS is a primary concern. If you are connecting an office of PCs to a LAN with servers, you need to configure the remote LAN VPN top use at least one of the remote DNS LAN servers in order to be able to resolve hostnames on the remote LAN. We would not recommend setting local machine DNS servers to the remote LAN DNS servers as this will stop normal operation of the computer, but the first server DNS server entry in the VPN network configuration adapter should be set to the remote Windows DNS servers.
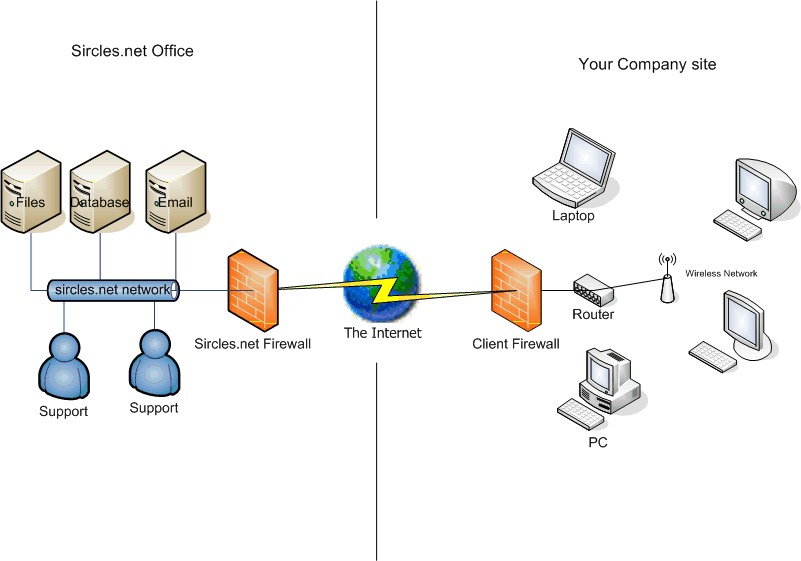
In the above image, the remote network, has only client machines, but uses the remote network for multiple hosts. The client machines therefore need the remote LAN DNS server set as their primary DNS server whilst they are connected to the VPN. The settings to configure the DNS for an individual VPN connection are under the VPN adapter/connection in Control PAnel > Network and Internet > Network and Internet > Network Connections. You can set the DNS servers under the Networking tab:

Which should be set to the internal addresses of the DNS servers thta will be accessible once the VPN has been established:


This way the client machines on the remote router network are able to find the email server and databases but if the VPN drops they can still connect to the secondary server to browse the web from the local router because the system will revert to the local DNS server addresses once the VPN is dropped.
LAN-to-LAN
In more complex configurations, there may be servers at each end of the VPN tunnel, and there may be domain trusts involved due to companies merging etc. In these cases the DNS servers need to be configured to share their network zones amongst each other. This is a very simple process but you will need the LAN IP addresses of all of the DNS servers before you start. Best practices suggest that you allow only the IPs of known DNS server to access the zone data from your DNS and this can be configured from the DNS server admin on each Windows DNS server. Once you have given permission for each server to access the DNS servers at the opposite end of the DNS tunnel, the clients of each interconnected LAN will be able to locate hosts at either end. If there is a Windows Trust in place then the client machines of each LAN will be able to access assigned documents and resources on the servers at the other office without any need for internet facing servers on either LAN.