Firstly let's set-up the Watchguard XTM Firebox:
I will use the software management rather than the browser but either will suffice if you stick to the correct encryption and key values.
Start your policy manager and click on the Branch Office Gateways option so that you are presented with the following:
To add a new Branch Office Gateway, click the 'add' button to open the Gateways properties box to enter the details:
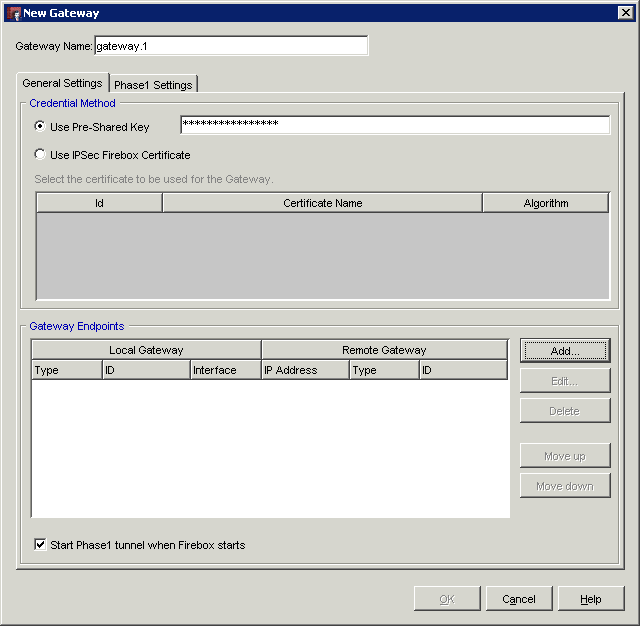
We are going to use a shared key with AES (Advanced or American Encryption Standard) encryption (or rather Rijndael encryption, invented by Vincent Rijmen & Joan Daemen) . Once entered (this must be identical to the shared key we are to enter in the DrayTek) click the 'add' button bottom right to enter the gateway endpoint:
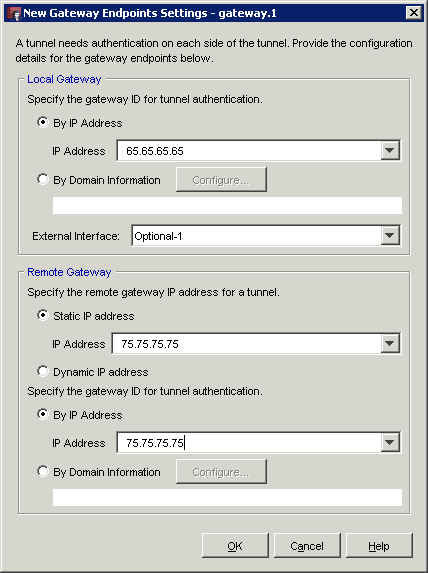
In this example the external IP of the Watchguard is 65.65.65.65 and the DrayTek is 75.75.75.75. So for the remote gateway (the endpoint remote from the Watchguard we are configuring) we enter the DrayTek external internet facing interface IP and for the local gateway, we enter the external interface IP of the Watchguard. We also use the external IP address of the DrayTek as the means of authentication of the gateway as you can see above. The optional-1 value in the above is the external interface of the Watchguard, so if you have a configuration with multiple internet gateways, make sure you are choosing the correct interface you wish to use for your endpoint, with the correct IP.
Say OK to complete this page.
Now that we have returned to the previous dialogue, click on the Phase 1 tab at the top, and you will see the dialogue below, where to configure Phase 1 settings for the VPN:
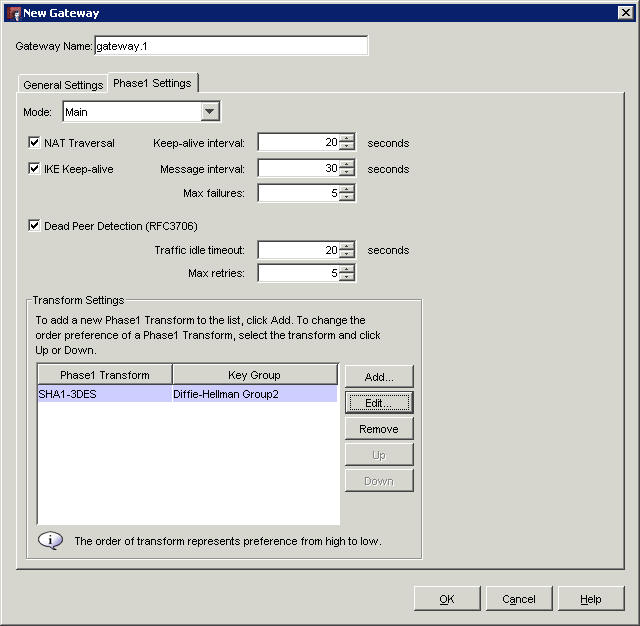
Tick the boxes for IKE keep alive and dead peer detection, then click 'Edit' at the bottom to edit the encryption settings:
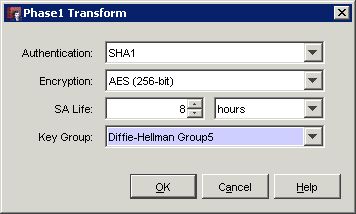
Select AES on an 8 hour time out as this will then match the default settings on the DrayTek.
Click OK and OK again to return us back to the Policy Manager, then click the VPN menu and select Branch Office Tunnels:
Click the 'add' button to add an IPSec tunnel:
Click the 'add' button to bring up the settings page for the tunnel:
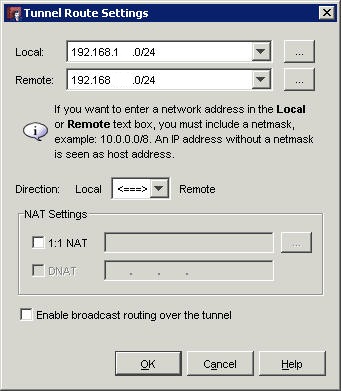
Here we are adding the internal IPs using 192.168.x.x subnets, we enter the local Firebox subnet and the remote DrayTek subnet with the /24 255.255.255.0 Class C subnet. When you are satisfied that you have correctly matched the local Watchguard subnet to the local subnet and the remote subnet to the DrayTek LAN subnet, click OK to complete the dialogue.
From that previous dialogue, select Phase 2 to be greeted with the below dialogue box:
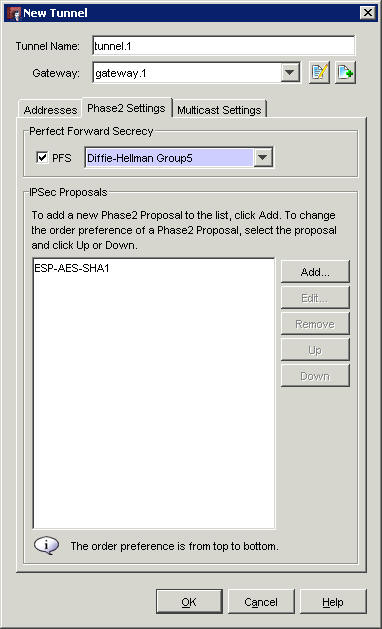
Tick the PFS (Perfect forward Secrecy) box and choose Group 5 as this is what we shall configure on the DrayTek.
We are sticking with the pre-configured ESP-AES-SHA1 IPSec proposal here, as it is sufficiently secure and compatible for connecting with the DrayTek. You may choose a custom configuration here, just be sure to note every setting so that it may be mirrored to the DrayTek, as any differences will cause the VPN to fail.
Click OK to return to the other screen
Click close on the tunnel screen to return to policy manager and save the settings to the Firebox.
Now we will configure the DrayTek 2860
Log in to the DrayTek web interface:
Under VPN on the left, click on the LAN to LAN settings subsection:
Click on the 1 hyperlink to open the LAN-to-LAN dialogue to see the below:
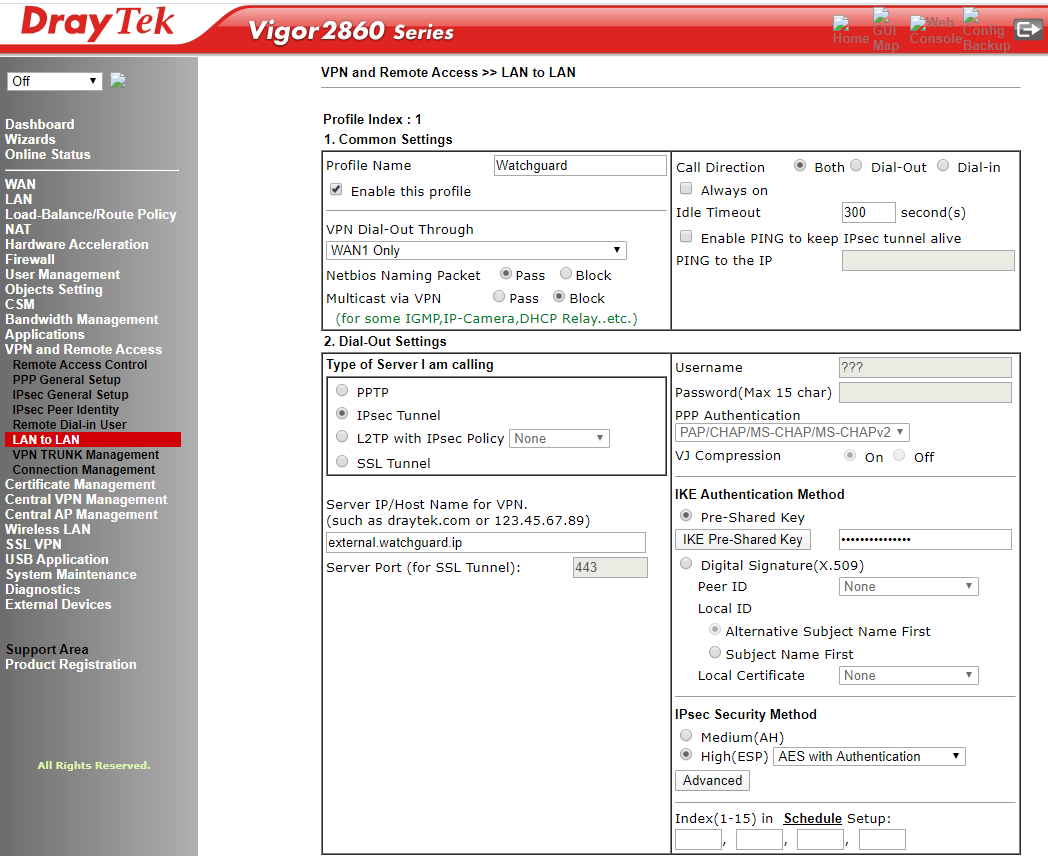
Tick the enable box to enliven the profile, then chosen to accept NetBIOS traffic so that peer-to-peer Windows network traffic can traverse the VPN. For the Server IP/Host Name for VPN box, add the external IP of the interface that will be the other endpoint of the VPN. For the call direction, in order that either end of the network can initialise the VPN, we have set to 'both' so this VPN will only be active when requested by either endpoint. Now click IKE Pre-shared key and enter the PSK exactly as you entered it into the Watchguard Firebox.
Next choose AES with authentication under IPSec Security Method and click on the 'advanced' button:
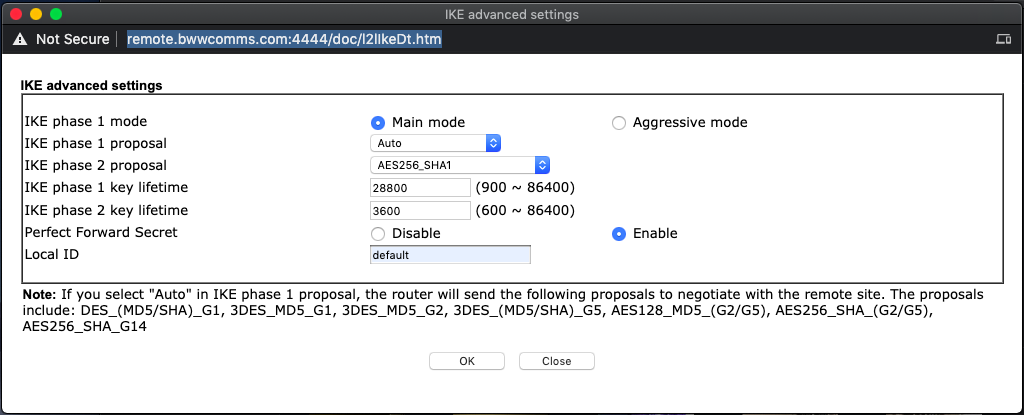
We are matching the settings on the Firebox - an 8 hour timeout (28800 seconds) with AES 256 bit SHA1 encryption and a perfect forward secret. Default will suffice as the Local ID for authentication.
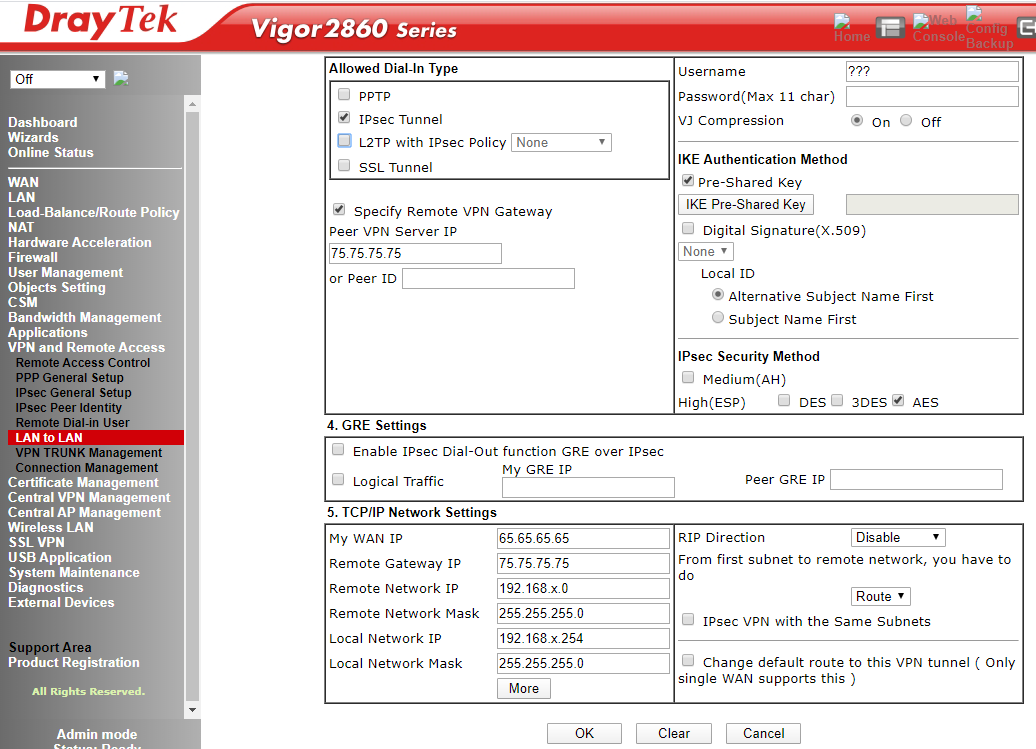
Choose IPSec as the dial-in type, then tick the specify remote VPN gateway as the Watchguard has a static address. We add the static address of the Watchguard WAN as the remote gateway endpoint, mirroring what we configured on the Watchguard earlier.
Click the IKE pre-shared key button and enter the pre-shared key once more; then enter the local and remote WAN and LAN details. Under IPSec Security Method encure that the AES options is the only box that is ticked. My WAN IP is the external IP of the DrayTek 2860 interface that will provide the other VPN endpoint to the Watchguard. The Remote Gateway IP is the interface external IP of the Watchguard VPN endpoint. The Remote Network IP is the subnet of the remote internal LAN behind the Watchguard that is being coupled with the LAN behind the DrayTek Vigor 2860. Correspondingly, the local network IP is the internal LAN behind the DrayTek that we are coupling to the Watchguard remote LAN. The subnet masks were both class C LANs, which you can see above.
Once all the values have been entered you can say OK and the always on VPN should pickup immediately...
Try pinging an internal IP of a host on the LAN behind the Watchguard from here:
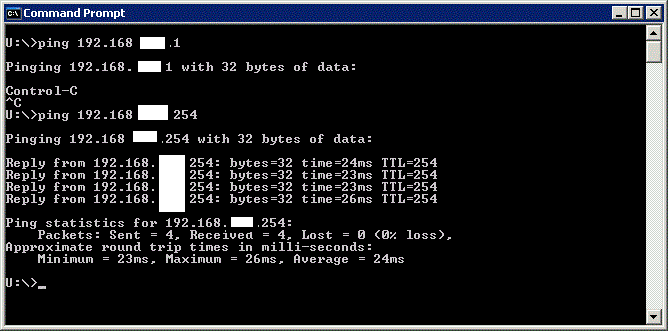
We can see the properties of the VPN on the Watchguard System Manager:

Buy DrayTek Vigor VPN routers here