DrayTek Vigor 2830/2860 to 3300/V/+ router IPSec VPN
This example is for an environment with a static IP at each office.
Firstly let us set-up the 3300 head office router:
After logging in, go to the VPN menu, then to IPSec and then to 'Policy Table'
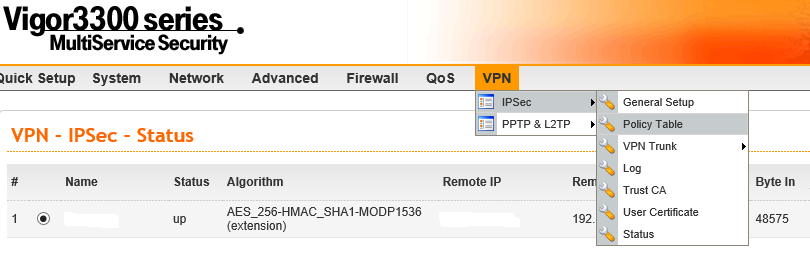
In this example we are going to use AES encryption with authentication for the maximum security available.
Firstly we enable the profile.
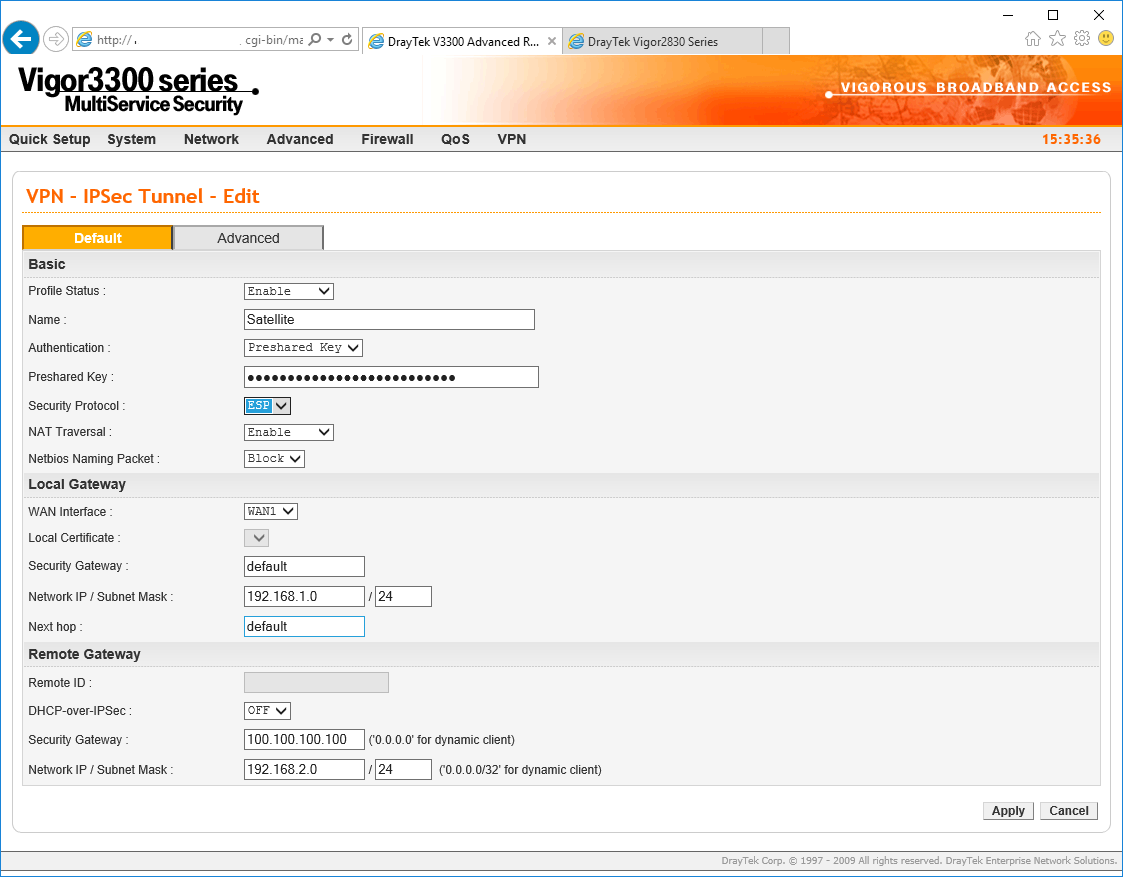
We name the profile something that explains the VPN and then we choose pre-shared key, which in this example is our preferred security key. Our security protocol will be ESP and we choose NAT Traversal to be enabled. In this example I am not enabling NetBIOS but if you are adding a VPN to extend a Windows domain then you should choose Pass here.
As we are connecting to another DrayTek device we are not going to change the default timeouts but if you do, they must be mirrored at each endpoint. We will change the security settings though, to ensure AES256-sha1 encryption and authentication.
We are ticking the PFS Perfect Forward Secrecy box also:
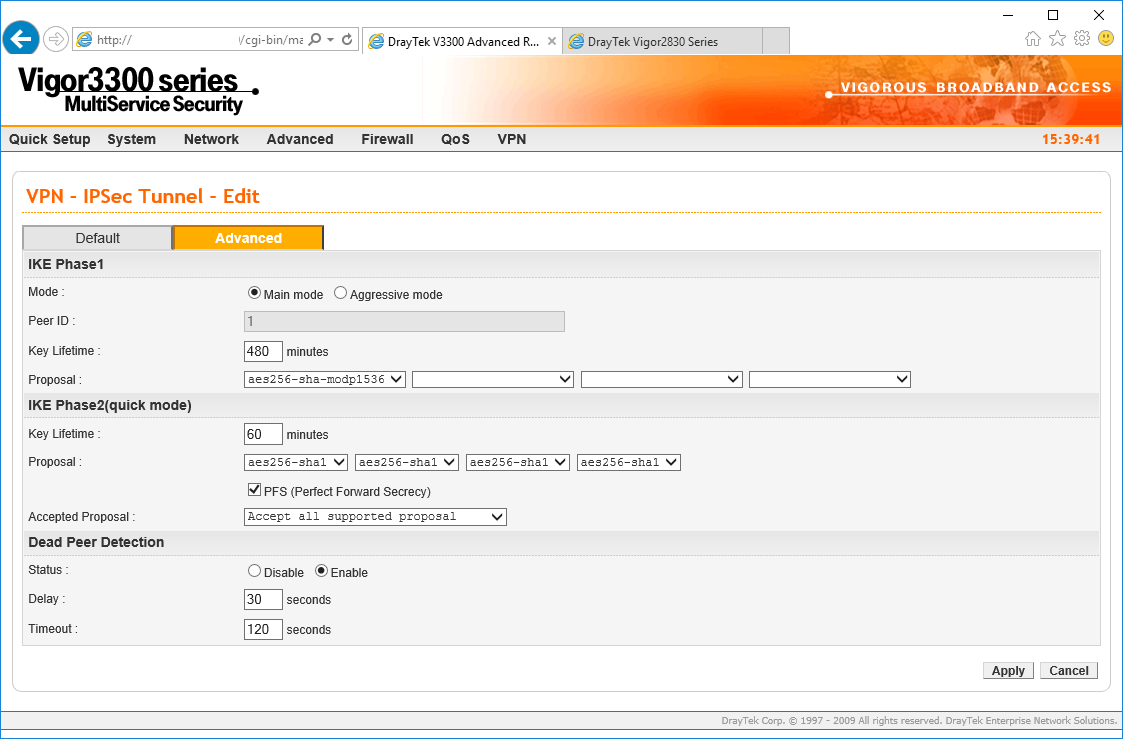
Now we can click Apply and configure the DrayTek Vigor 2830/2860...
Under the VPN menu, go to Lan to LAN to set-up your connection to the DrayTek 3300
Click the number corresponding to the first available unused profile...
Now we are going to enter the details required to connect to the 3300 router:
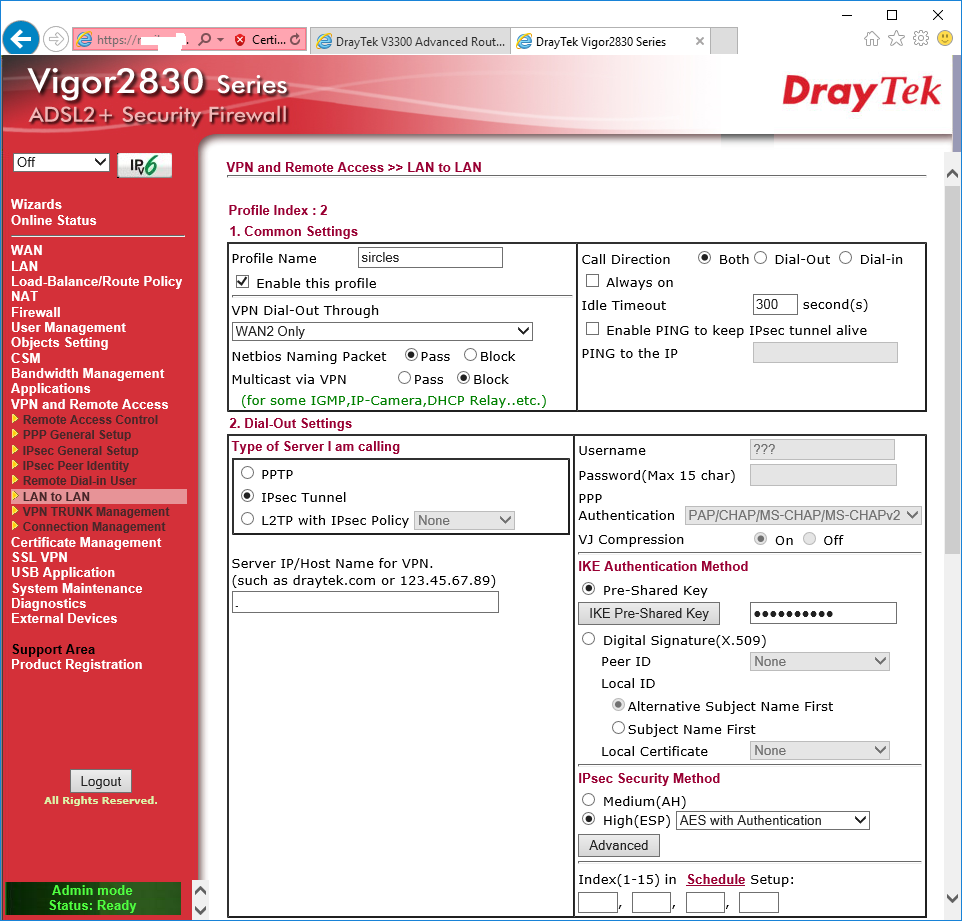
We are once again giving it a name relevant to the connection. In this case we are connecting through WAN2 but you can choose WAN1 if you are using ADSL/VDSL
NetBIOS should be enabled/disabled depending on whether you are allowing file access to Windows machines across the VPN. In most cases with Windows machines you would pass NetBIOS packets.
The call direction is set to Both to allow either end to start the VPN.
Under Dial-Out settings we set the VPN type to IPSec once again.
We enter the domain name/ip address of the external interface of the other 3300 router in the box below.
We now tick the Pre-Share Key box to the right and click the Pre-Shared Key button to enter the same key as we entered into the 3300 Pre-Shared Key box.
Below that we select the High(ESP) option and choose AES with Authentication as we did on the 3300
Now click the Advanced Box:
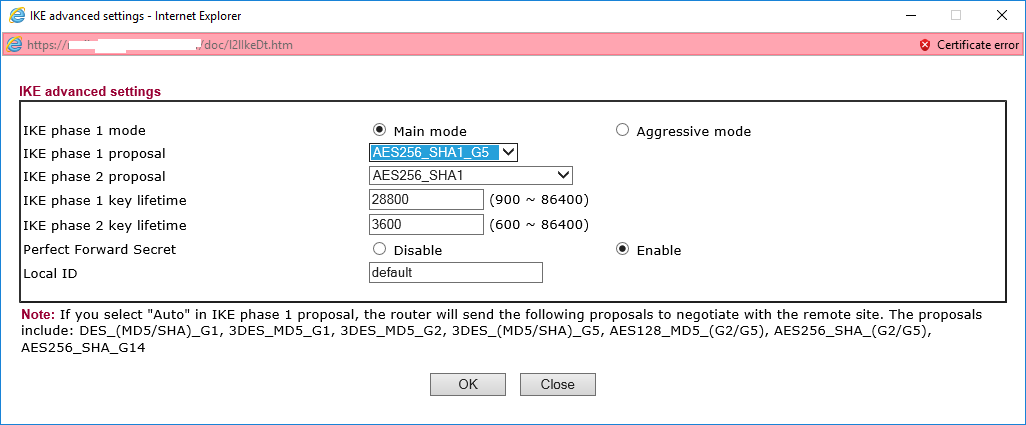
We are mirroring the settings from the 3300 here so we choose the AES256-SHA1_G5 for phase one and AES-256 for the phase two proposal.
Once again we select the Perfect Forward Secret option and the timeouts are already consistent.
Click OK when done.
Now under IPSec security method, tick only the AES box and then enter the IP address details at the bottom of the page:
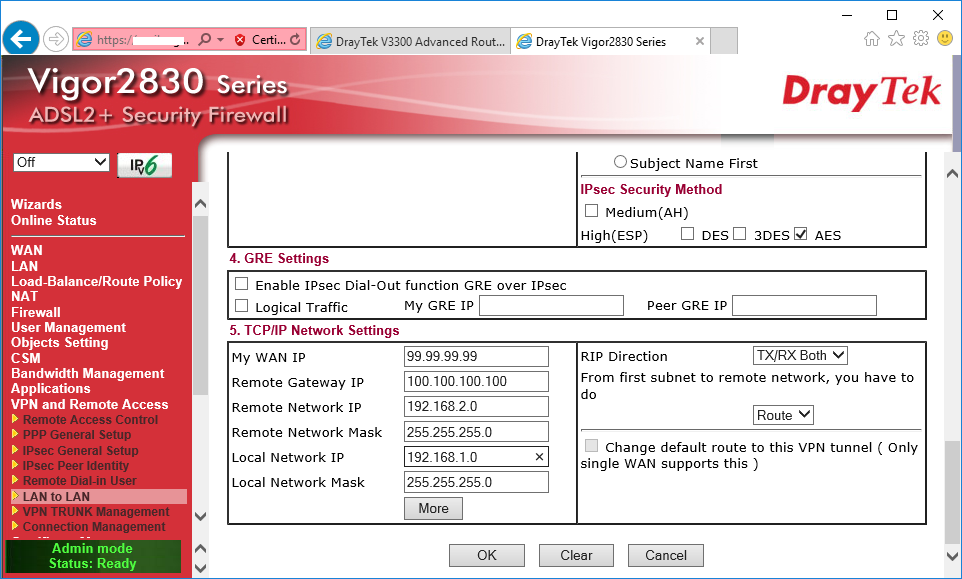
We enter the external IP of the 2860/2830 first in the My WAN IP box.
Enter the remote 3300 router external interface address in Remote Gateway IP addres box.
Then enter the remote DrayTek 3300 internal network subnet details in the two boxes below that.
Finally enter the DrayTek 2860/2830 local network subnet details in the two boxes below that.
Click OK when done.
Now under VPN and Remote Access on the 2860/2830 you should see the connection as live:
