Your computer is on a network as soon as it is on the Internet, as soon as it is connected to any other machine we are dealing with a network. When you are dialling into anywhere you are creating a network as you go with your modem being assigned an address in order to enable communication; an address is assigned to your computer just so the other bodies you request information from can be routed back to you. The truth is that networking these days is so seamless that you may think that there is not really any reason to look into the nuts and bolts of it all unless you are interested in becoming a network engineer or a developer. The simplest computer networks though, all follow the same ideas which begin with a very simple model that is divided into 7 layers:
The 7 Layer OSI Model is a description of how a network works. Although one technology might span a number of layers or not even span one, it is a very useful and precise way of deciding what is going on and where. Whenever we are using networks the communication starts at us - the user - and moves down through the layers of the computer network model and then back up again to reach another user or back to us with the information. If this seems unclear then let us have a look at an example.
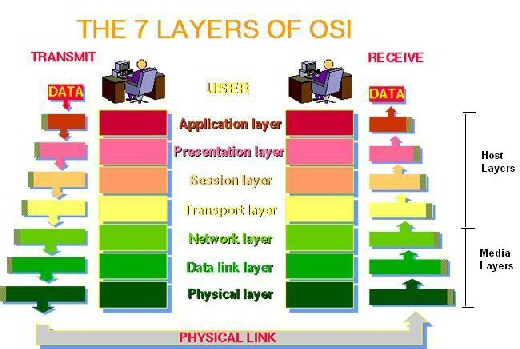
Graphic is taken from The Abdus Salam International Centre for Theoretical Physics.
Above we can see that each user is at the top of the seven layer model. In order for the system to function, i.e. for data to travel from one user to the next it must successfully descend to the physical layer and back up to the next user, negotiating every level one after the other in each direction. As it was stated previously, the model is really just a useful way to divide up each level of functionality in order to design systems or diagnose problems but let us have a look at where each level lies in a few examples of us using a computer.
The Application Layer is where all of the Application-specific and user processes occur that we experience as users. All data here is used specifically by an application and will most likely be in a format that only certain applications can understand like *.doc or *.xls files. FTP and Telnet are entirely in this region as they are applications communicating a particular type of information specifically for other telnet or FTP users respectively.
The Presentation Layer (Also the Syntax Layer) is a conversion layer providing abstraction for the Application Layer so that all traffic can be sent across the network available to be understood by all and then being reconverted back to the Application Layer when received. This layer provides formatting and encryption to enable the data to be sent across the network, and then un-formats and encrypts data that is received. MIME, Encryption and Compression all occur at this level.
The Session Layer controls the sessions started and stopped by requests from the Presentation Layer, more easily thought of as managing dialogue between the layers above and below. All sessions are opened, managed and terminated by this layer.
The Transport Layer is responsible for transporting data between hosts and is entirely transparent - i.e. none of the services using this layer able to communicate with or detect the layer itself. All endpoints on the system are connected by the transport layer which controls flow control and ensures complete end-to-end data transfer.
The Network Layer provides routing technologies, creating logical paths, known as virtual circuits, for transmitting data from node to node. The network layer provides the functional and procedural means of transferring variable length data sequences (packets) from a source to a destination via one or more networks while maintains the quality of service (QoS) requested by the Transport layer. The Network Layer also performs error handling, addressing, inter-networking, congestion control and packet sequencing. Routing and Forwarding operate at this layer -- sending data throughout the extended network and making the Internet possible (there also exist layer 3 (or IP) switches). This is a logical addressing scheme - values are chosen by the network engineer. The addressing scheme is hierarchical. TCP/IP which we all use to connect to the Internet relies on the reliability of all of the error handling and packet sequencing managed by this layer, the IP part (Internet Protocol) is genuinely perceived to be layer 3.
The Data Link Layer is where Ethernet resides. This layer is capable of detecting and sometimes correcting errors in the Physical Layer. MAC and LLC are the two partnering components of this layer, MAC addresses are hard coded into each node of the network and the MAC (Media Access Control) governs how a device on the network gains control to data and whether or not it may transmit data of it's own. The LLC (Logical Link Control) governs frame handling, flow control and error checking.
The Physical Layer is the hardware carrier control and provides the physical means of transmitting the Bit Stream down cables or across Microwave or Infrared etc. Ethernet Hubs are Layer 1 as they simply re-transmit received signals to every other port of the Hub. SCSI devices are also examples of this layer and Fast Ethernet, ATM and RS232 are protocols with segments occurring in this layer.