This scam is all over the place at the moment, and concerns only people who already have Bitcoin and are being targeted to deposit a small sum in order to ostensibly receive a much larger reward. The system works something like this. You receive an email that takes you through to a Google drawing that consists of something like this:

The drawing is just a shortcut to a website that attempts to defraud you as below:
So the pattern is that you are taken through to some sort of company that represent some type of poorly defined group that send =each other cryptocurrency for sketchy reasons. This 'group' will often infer that you have received the email in error so as to make you believe you are about to receive Bitcoin due someone else. This is a tactic to prevent you from reporting what happens.
Another part of this scam is that the amount of money is not huge, it is a few hundred dollars, and so their is not a huge impetus to recover the funds as with a boiler room scam. This scam is about volume, and about automation. They have moved away from call centre scammers and towards automated online scamming systems. This whole system is nothing more than an animation that pretends you have received Bitcoin and that all you need to do to receive $30k of bitcoin is to pay $249 worth. It is that simple.
This system is far more difficult to trace than previous boiler room-type scams, as there are no accents to listen to, no phone numbers to query, and no questions to ask. it is just a website linked from a Google drawing that is hidden behind proxies and privacy companies and is difficult to even begin to seek out. Let's see how far we can get anyway.
How does the Bitcoin Transfer Scam Begin?
So here is a typical email from the scammers:
From: mancine xz7x <[email protected]>
Sent: 11 August 2023 09:36
To: Steve FcKay
Subject: ?? Personal Notification.TRANSFER 0.7372416 BTC
Dear user!
? Personal Notification for ID[N2PZ8X14]
? Previously, we notified you by email about the receipt of a crypto transfer in your name.
The sender is an online crypto service , the recipient is your email address.
https://docs.google.com/drawings/d/1vPAOao2E2Od1jpHH22egIkjSobrmOkWqw7oHsYUd6yA/preview?991tz3360
The message is a bit garbled, but it seems to be saying that we have received some sort of incoming transfer of Bitcoin, but it does not appear to be to our wallet, but to some unknown service that has chosen us by mistake. It just states that 'the sender is an online crypto service' and we're not sure what other type of crypto service that you could ever have, but let's see where it takes us.
So we can see that the link takes us through to: https://docs.google.com/drawings/d/1vPAOao2E2Od1jpHH22egIkjSobrmOkWqw7oHsYUd6yA/preview?
Now this is just a preview, as you can see from the URL above. If we remove the code subsequent to the forward slash, we can see the actual Google document and report it, as below:
So, now that we can report these links, let's find out what the scam actually consists of: We are sent through to a website with URL https://paymetev.stimularcrypto.website/info/
|
The first thing we see is actually described as a burn notice which usually means that something is to be destroyed before certain people are able to read or access it. There is even a ringing bell in the top corner to increase urgency and today's date is given as the expiry, ensuring maximum panic; this is undoubtedly a scam.
We're not sure what 'Please receive a translation' is actually supposed to mean, but we think that they probably mean 'transaction' rather than translation as if you don't read English anyway, why would you be able to read that?
|
The get transfer button takes you through to the rest of the scam, which is on a file called server.php which then takes you through to num1a-komisbilling.php, whatever that means.
Here is where the animation takes you through the supposed transfer process:
And brings you to the part where you have to pay in advance to receive your (or rather someone else's) Bitcoins:
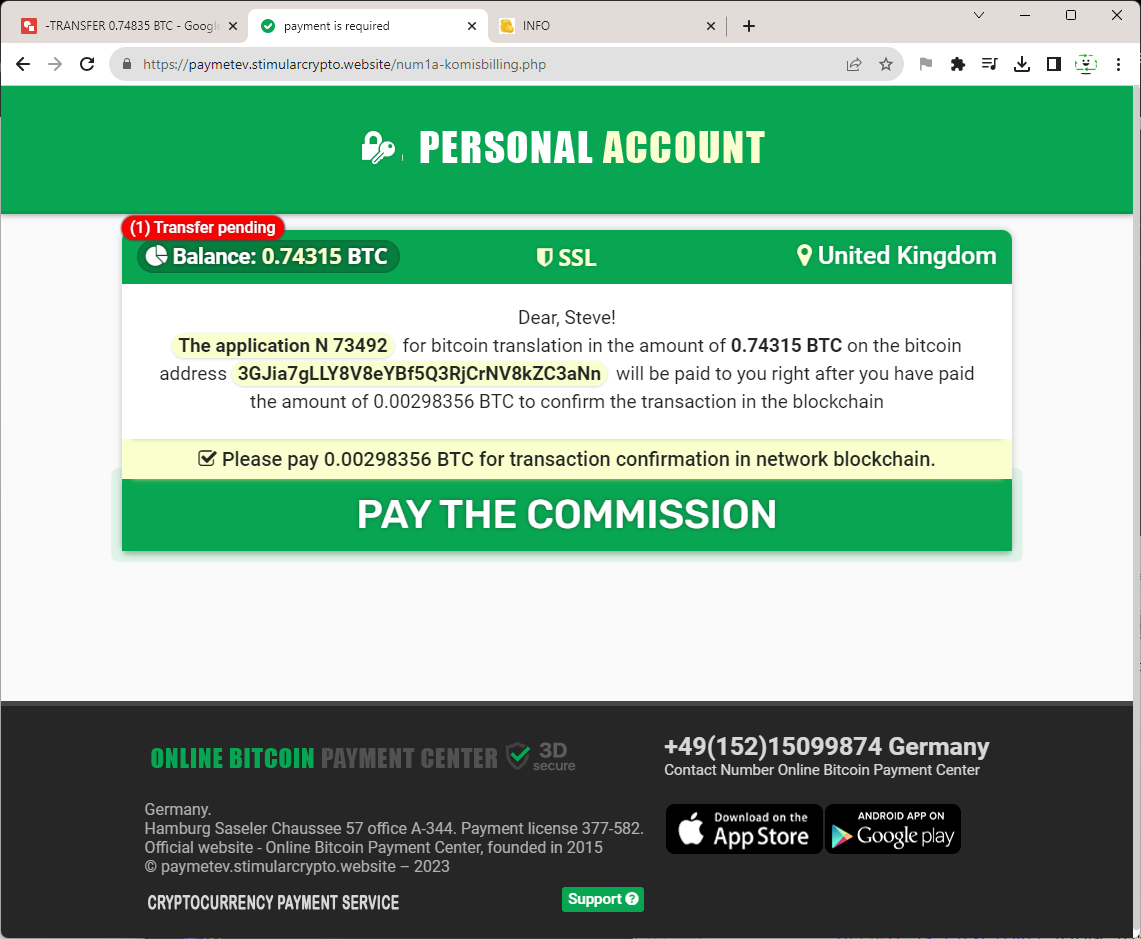
Which takes you through to a payment service: https://paymentsvip.gq/

This is a real payment that you have to make in BTC and this is where they take your money. As we said earlier, there is now no human element in the scam at all. It is completely automated and very hard to trace. Let's see if we can find out anything about the different elements of the scam.
Firstly, let's start with the domain. Who are stimularcrypto.website?
Whoisology finds nothing:
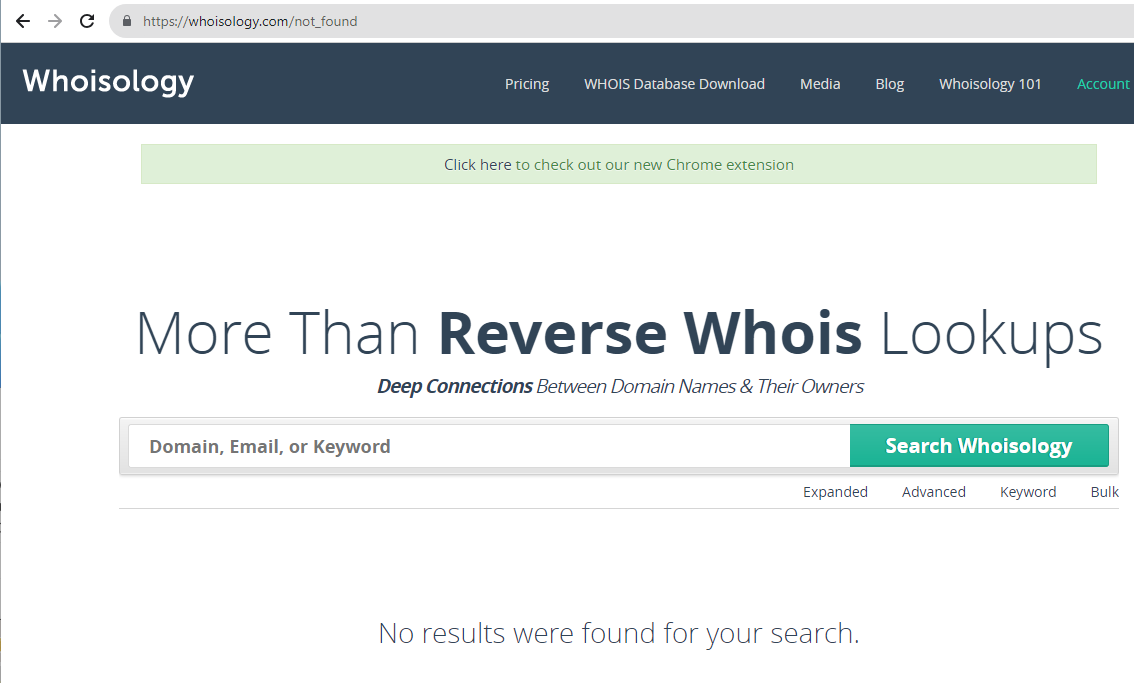
Which is very odd, this domain is registered somewhere really obscure and unseen.
Who.is finds nothing either...
Domaintools.com finds:
| Registrar |
PDR Ltd. d/b/a PublicDomainRegistry.com
IANA ID: 303
URL: https://publicdomainregistry.com
Whois Server: whois.PublicDomainRegistry.com

(p) |
We have emailed details of the website to them in the hope that they will take action.
The IP address appears to be 95.142.40.55 so what is that?
Well according to RIPE, there is this:
- inetnum: 95.142.40.0 - 95.142.40.255
- netname: EUROBYTE-NET
- descr: Eurobyte VDS
- country: RU
- admin-c: EL2290-RIPE
- tech-c: EL2290-RIPE
- abuse-c: EL2290-RIPE
- status: ASSIGNED PA
- mnt-by: EUROBYTE-MNT
- mnt-by: MCHOST
- created: 2017-08-02T05:54:35Z
- last-modified: 2018-11-20T09:40:47Z
- source: RIPE
- route: 95.142.40.0/24
- origin: AS210079
- mnt-by: EUROBYTE-MNT
- created: 2018-11-22T05:45:23Z
- last-modified: 2018-11-22T05:45:23Z
- source: RIPE
Who are:
- role: EuroByte LLC
- address: 109387, Moscow, box 20
- address: RU
- remarks: EuroByte contacts
- remarks: ---------------------------------------------------
- remarks: SPAM and Network security issues: [email protected]
- remarks: Customer support: [email protected]
- remarks: Legal address: 109387, Moscow, Lyublinskaya str, 42, office 507
So they are not masking their IP by the look of it, so we can at least send a report to Russia regarding this website.
Привет
Пожалуйста, вы можете взглянуть на этот сайт:
https://paymetev.stimularcrypto.website/num1a-komisbilling.php
Это поддельная афера с переводом биткойнов.
Пожалуйста, удалите, если считаете это мошенничеством.
Спасибо
Hopefully they can shut it down if it really is on that IP address.
But what about the payment gateway? Do they really allow this kind of behaviour, or are they just in the dark as to what is happening?
They do not appear to have an obvious website:
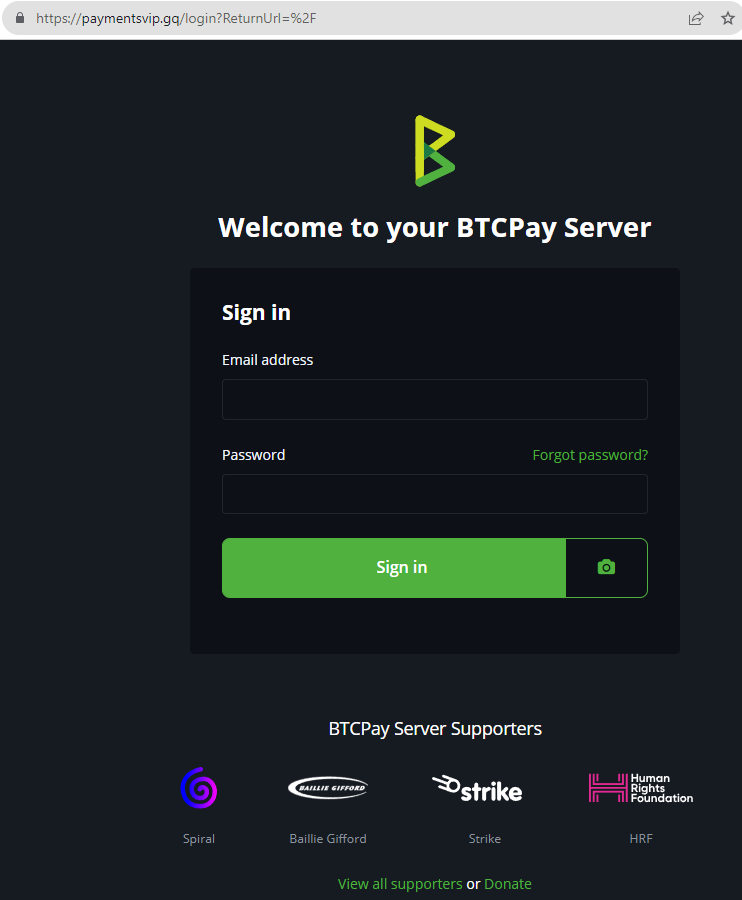 |
Let's see if we can find anything out about them. The code is based upon btcpayserver which is an open source bitcoin payment server available to download and customise online. You can see it on github here: https://github.com/btcpayserver/btcpayserver where they give a description and technical details. This is not leading anywhere. The issue is that BTC payment does not require connection to the banks and so can be completely independent and free of regulation which is the blessing and the curse of cryptocurrency.
So the payment domain may also belong to the same scammers, let's see if they have left any sign of their identities there. Unfortunately this is the same result as before. No direct data apart from the registrar can be derived, who are here:
Your selected domain name is a FREE Dominio GQ domain name
Equatorial Guinea Domains B.V.
Dominio GQ administrator
P.O. Box 11774
1001 GT Amsterdam
Netherlands
We have contacted the hosts and the registrars...
|
Anyone telling you that you are receiving crypto currency you are not expecting is a SCAMMER!